I agree, it is not as honourable as regular fishing, but the returns are far better, considering the time and effort invested - especially since one does not have to even lift a finger to send thousands of [unsolicited] emails.
Landing a big catch can mean early retirement!
Now that you are hooked, let’s start with the types of phishing, based on target selection.
Spam vs. Phishing: What's the Difference?
Spam is bulk, unsolicited messages—usually annoying but mostly harmless.
Phishing is a targeted attempt to steal sensitive information, like passwords or credit card details, by pretending to be a trusted entity.
Key Difference
Spam clogs your inbox; phishing threatens your security.
Stay alert: avoid clicking unknown links, and always verify the source.
Casting a net
These are generally low effort and easily detectable for someone who is even barely computer-literate. And yet, they work because the impulses of the average plebeian tend to get the better of them.
The emails in this category have most (if not all) of the following characteristics:
● Spelling mistakes
● Poor Grammar
● Pictures of money
● hot singles
or the other sins (well, sex sells)
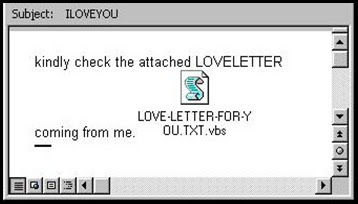
Not everyone falls for fishy emails, but remember: for such manifestations of criminally lethargic malice, finding one fool in a million who would part with his money would likely result in a breakeven.

What is the matter? A few people did not swallow the bait? No need to get salty about it.
Remember: there are plenty of fish in the sea, so keep trying!
Keep in mind though: the more aggressive your… er, campaign is, the higher the chances of automated spam detection catching you. They tend to be smarter than the humans using them. So keep it low-key and not like Loki.
Spear phishing
The risks are higher, but so is the reward (as well as the skill requirement)!
Spear phishing necessitates one to do some homework on the target, like:
● workplace
● banking partner
● family and friends
● pets and hobbies
● side chick
With information like that, a spear phisher can craft lovely messages (it can be via email,SMS, or even postage) expertly tailored for the target.
I know, I know, it is not easy, but trust me - the hard work pays off. Sometimes.
Think about it: how hard can it be to impersonate a person’s account (hereon referred to as the subject)? How about doing some stalking, oops, OSINT (Open Source Intelligence)?
● Obtaining the subject’s profile picture - in this day and age, who on earth would dig through the settings and that too to restrict access to the profile picture? Right click, save image and the attacker has the profile picture.
● Locating the subject - Multiple avenues here - LinkedIn profiles are a Google search away, and they generally specify the city in which they work in. Also, people love posting pictures with a very informative background.

● Discovering the subject’s interests - we live in a world where what a person had for lunch is worth publishing on the internet. For likes and validation. It wouldn’t take the attacker long to figure out what the subject likes, and perhaps even what (s)he hates
● Finding how the subject pays their bills - LinkedIn is your friend. Workplace, job title, recent achievements, the boss’ name - they have it all.
Low-effort spear phishing
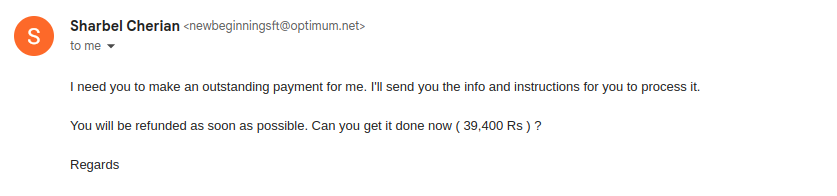
Emails like the above were sent to multiple people in my organisation, particularly to those who just graduated from university; supposedly because they’re too young and naive. I approve, however - from an attacking standpoint, that is!
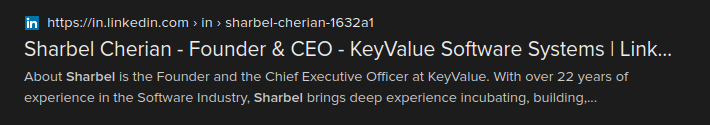
It’s safe to say the attacker did some research, but their technical proficiency was lacking (or, they got complacent and underestimated us).
Let’s start with the address: newbeginningsft@optimum.net. Apparently the email address of the CEO, ladies and gentlemen.
Email display name
They could have tried sharbelCEO@optimum.net, sharbelkeyvalue@optimum.net or even valuebelsharkey@optimum.net, if the perpetrator wanted to test the limits of creative licence. Somebody decided to lower their standards by simply changing the profile name (the link is for Google accounts).
Here’s a quick demonstration:
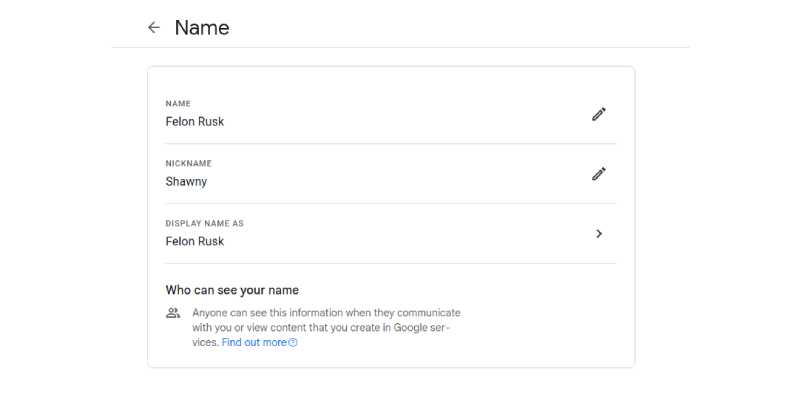
Now, when I send an e-mail to somebody, they don’t see Shawn Mathew, it’s Felon Rusk.
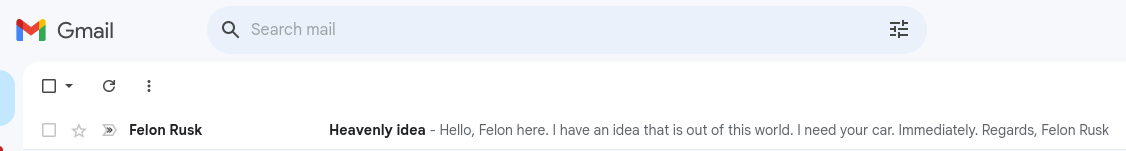
As you can see, it isn’t even marked dangerous, let alone sent to spam.
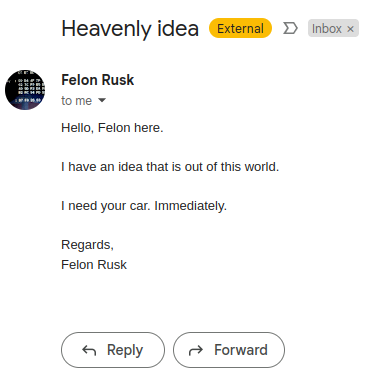
“The legendary Felon Rusk? I am gonna be famous! My car? Take it!” - the recipient. With luck, the recipient’s car will end up in space, alright. My parking space.
Optical illusions
If the attackers wanted to take it up a notch, they could’ve used a domain that looks very similar to the original domain. For example, an attacker can attempt to use an email domain like b00k.com to phish people working for book.com. Up close, they look slightly different, but the same can’t be said when the average joe is skimming through 5-10 emails at his 9-5 job counting down the hours before he can go home.
Advanced spear phishing
There’s something about instant messaging that tends to make it more effective, for phishing and otherwise!
Perhaps that is owed to the following reasons:
● The “Instant” in instant messaging naturally evokes urgency. Most apps will make it obvious - the flashing ‘notification light’, notification sound and the screen turning on.
● Instant messaging is incredibly fast and convenient, compared to emails. There’s
pressure to respond immediately, lest you want to come across as a snob.
● People tend to expect spam & phishing messages only via e-mails. Many examples available on the internet are screenshots of emails.
● The relatively small display and font size increase the likelihood of the user missing important details. Like the ‘upto’ in theSALE! 90% discount banners.
The following example involves an attacker using Facebook Messenger as the medium.This attacker impersonated the account of the victim’s cousin who works in ‘murica.
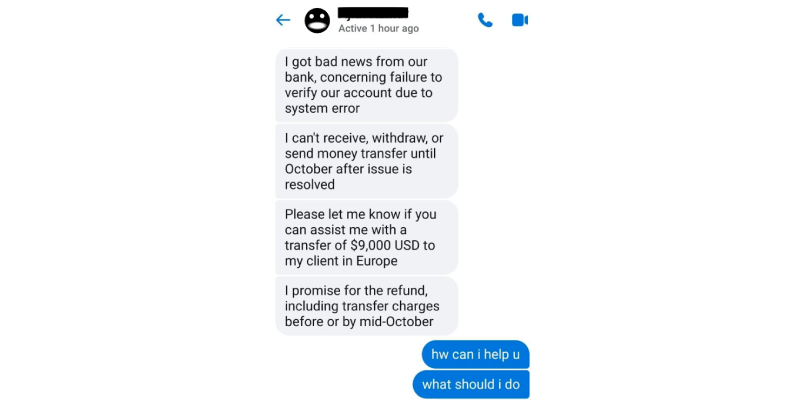
I must say, the attacker has got it well structured: There’s an introduction to the problem and the ramifications of it followed by clear instructions and even a guarantee with an estimate!
I’d say the attacker succeeded in creating the urgency of being penniless in a foreign country in an exceptionally clear, concise and an easy to follow-through fashion. Only if doing the taxes were that simple!
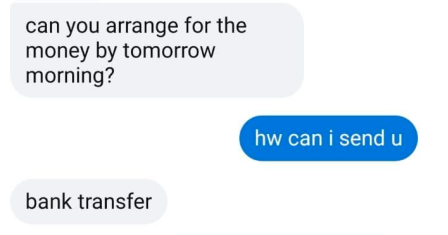
Please do not send money to the above account.
(Do not judge me, warning labels exist for a reason).
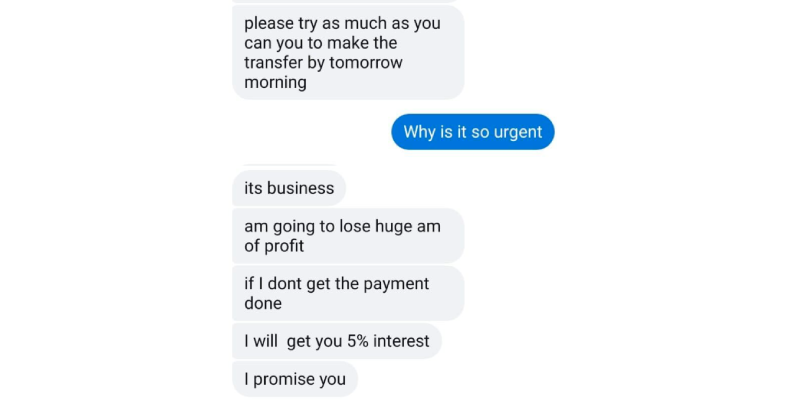
The attacker is subtly persuading the subject to make the transfer by the next morning, using the urgency to advantage.
Questioning the same results in even more urgency, along with a 5% interest being
promised. What an irresistible offer!
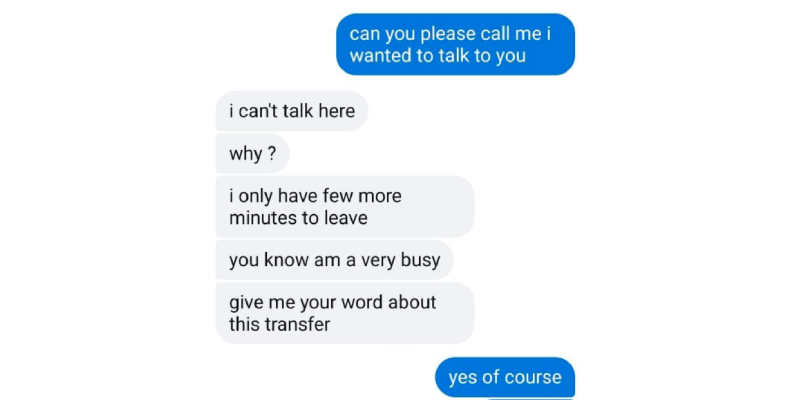
When a distant cousin makes a strange request like an extremely urgent loan of $9000 with the promise to pay back with 5% interest, it’s a good idea to call them. For three reasons:
● To ensure they didn’t message the wrong person
● To confirm they’re not intoxicated.
● Unless the attacker is a ventriloquist, the game would be over at “Hello”. Hence,
every effort would be made to dodge the telephone call.
Too bad the person the attacker was impersonating happened to be sitting right next to the supposed victim. Who is the victim now, eh?

Extreme phishing
A video is certainly worth more than a thousand words, so please watch this video of a well known but still effective attack.
Personally, I think he went too far with the attack. The victims must have been traumatised.
Author’s note
I don’t like seafood, nor prison food for that matter.
More importantly, this is not real hacking. This is just being emotionally manipulative to human beings, and not computer systems. Not so honourable.
You might as well write a love letter with your incredible skills. Make love, not war.
P.S: If you’d like to learn more about phishing, e-mail me with a picture of your bank card -for identification purposes, obviously!

